After analyzing what happened to his smartphone, it appeared that the only key to detect Jeff Bezos’ hack was to monitor data traffic to detect anomalous behaviour.
Usually, most of data traffic on a mobile device is download traffic: internet and social media browsing and visualization.
When looking into details, there are some apps that have a constant flow of background upload, whatever the use you are giving to those apps. We are talking about apps that silently send data to their home server, although the phone is actually not in use at that moment (background traffic):
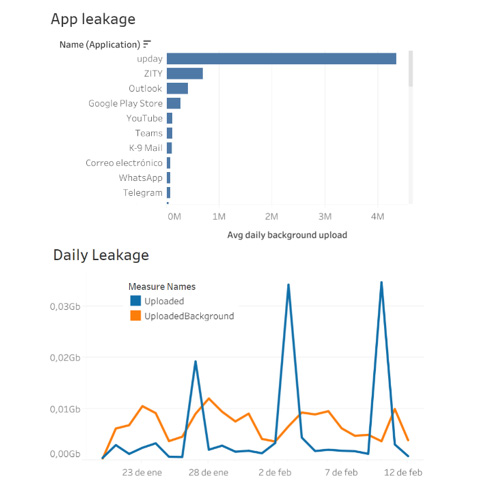
For instance, according to the data we collected from devices running Samoby Threat Defense, Facebook usually uploads an amount of 1Mb each day, without even using it. So does samsung’s upday (4mb), google play store, snapshat, whatsapp, spotify, and many others.
Some other apps have an intense background upload traffic when you use them. For example Google Photos uploads all your photos and videos whenever you shoot them, as does Instagram for example.
In all case, each user has a typical usage pattern, depending on the apps he has installed and usually uses. This usage pattern is typically made of a list of (app,upload volume, destination server), and metrics as simple as daily upload can be defined for each user profile.
Samoby gets all that info from each device, classifying users according to their usage pattern. Doing a real time behavior analysis of apps, data upload and download, storage usage, and other parameters.
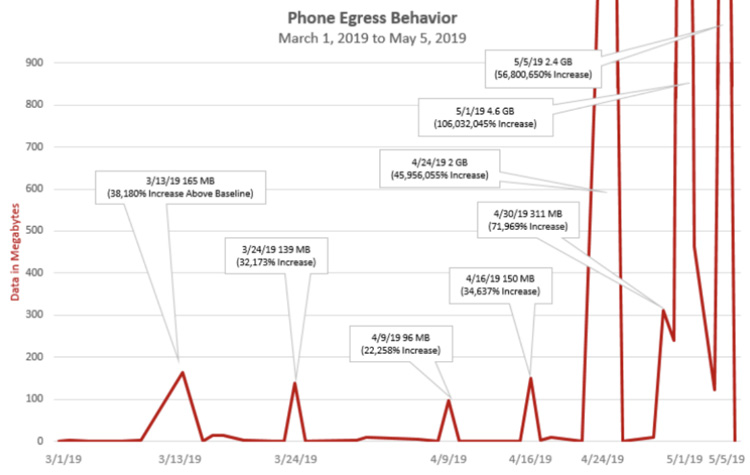
In Jeff Bezos’s case, before his phone got hacked, his usage pattern was that of a quite low usage of his phone: upstream traffic was usually less than a 1 MB a day, and during the last 6 months, the average volume of data uploads was around 15MB.
This drastically changed after his phone got hacked (presumably on May 1st 2018): peaks began to appear frequently at 100MB, 500MB, 1Gb and even 2.4GB on May 5th 2019.
Closely monitoring upload traffic is key to detect Jeff Bezos’ hack, for an early detection and mitigation.
Samoby enables you to have real time information about mobile device traffic, and set up alerts when upload traffic is anormally high during a short period of time.
Zero day attack are quite impossible to prevent, the only solution is to track phone unusual behavior and detect “symptoms” that an attacker has gained control over your device: Data traffic is one of them.
Samoby monitors a wide range of symptoms such as data traffic, root certificate install, DNS,… in order to help companies protect their assets against zero day attacks.
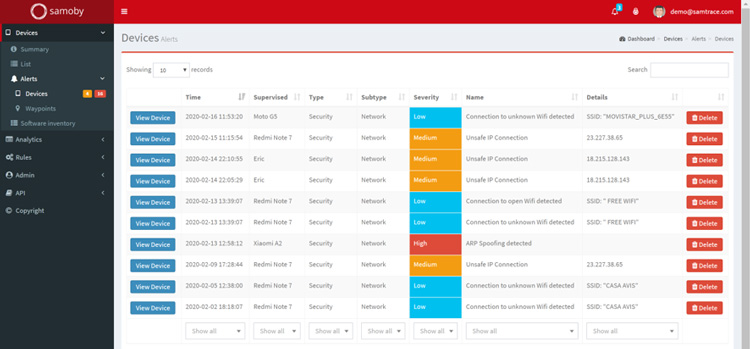
For example,
- IP traffic is scanned and connection from malware to C&C servers IPs can be blocked.
- Connections from apps to known privacy data leakage domains can also be blocked.
- When a new app is installed, it is checked and blocked if recognized as a malware
- Users are prevented from opening links to phishing sites or malicious URLs.
- Devices are checked for jailbreak/root, and mitigation rules can be applied if detected.
- and many others.


